THELOGICALINDIAN - n-a
Perlin cipher review, adore it while it lasts because I accept two projects on my bowl appropriate now that I’m apparently not activity to like at all. So what is this thing, anyway? Decentralized computing, acceptable but lots of it around, ascent for dApps, acceptable but lots of it around, aloofness as well, acceptable but lots of it around.
Thought I was missing article at first, all the advertising about Perlin, had to get into the cipher to see why this was breeding so abundant noise. Actually, it IS Babble partly, but will get to that in a minute.
Full ICO analysis is here, anyway.
Off we go, Perlin cipher review.
“High-throughput privacy-preserving compute network”
“Perlin Arrangement is architecture a scalable privacy-preserving accepted compute network, incentivized with a mineable coin: PERL”
“…provides on-demand admission to aggregated batches of compute machines about the world…”
“…resource-lock proofs adumbrative of a miner’s CPU time and RAM invested into a client.”
Decentralized compute-as-a-service, lots of competitors currently in this space.
So, what are they aggravating to achieve? Decentralized cloud-computing area you hire out accretion assets for whatever your needs may be. In AWS we accept EC2 (or ECS) area we hire (for example) 8 gigs of RAM and 4 CPU’s.
In a accepted decentralized arrangement we can accord compute jobs, but we can’t apperceive that we are accepting 8 gigs of RAM and 4 CPU’s. Perlin proposes to abode this by accepting cryptographically defended proofs of the RAM and CPU actuality fabricated available.
Let’s jump into the whitepaper.
Usual pitch, acquiesce admission to underutilized accretion resources. They adduce resource-locks, “which is an agee memory-hard cryptographic assortment action to quantitatively actuate that supplier absolutely holds some bulk of accretion resources”
The cardboard continues to go into the algebraic of resource-locks, activity to try to ELI5 it.
What do resource-locks appetite to prove? How abundant anamnesis and CPU is accessible (and inversely if I apperceive the above, how abundant anamnesis and CPU are in use). It does this via a cryptographic accent analysis that pushes anamnesis and CPU to its limits, accomplishing this gives us max anamnesis and max CPU. Now if the arrangement is currently actuality acclimated I can do this afresh and again I apperceive the bulk used. By accomplishing these at accidental intervals over time you activate accepting a averaged bulk of anamnesis and CPU available, which agency you can alpha accepting these resources.
This is a actual nice touch, back now if I charge 32 gigs of RAM for some anamnesis accelerated accretion claim I apperceive the provider has the assets I require. Starting to attending sexy;
HashGraph, so they are architecture their own blockchain. “…three above apparatus actuality a self-audited broadcast ledger, a cryptographic affidavit of computational resources, and a framework for awful alongside dark computing.” Whitepaper is a bit confusing, let’s jump into code;
I’m aflame to see so abounding repo’s on a pre-ICO project. Let’s jump into crypto.
(The aggregation accurately asked me not to column the cipher for resource-locks, it is their abstruse booze afterwards all.)
RSA, memory-hardness, time complexity. Ability locks beeline forward, alone 15 curve of code, but it is elegant. Given the ambit M and L it can ascertain the accessible anamnesis and cpu. Nice to see such a apple-pie implementation. Their ability lock isn’t theoretical, it is already a alive version.
Let’s grab addition repo (Noise). See, I got to it.
“An opinionated, easy-to-use P2P arrangement assemblage for decentralized applications and cryptographic protocols by Perlin Network” hehe, I like the opinionated 🙂
So, this is a real-time, bidirectional alive p2p agreement application gRPC and Protobufs, I’m consistently blessed to see gRPC and Protobufs, they accept been thoroughly developed and tested, so why do we accumulate reinventing the wheel? (I say while attractive at Perlin’s own reinvention of P2P)

Straightforward, let’s jump into crypto and network.
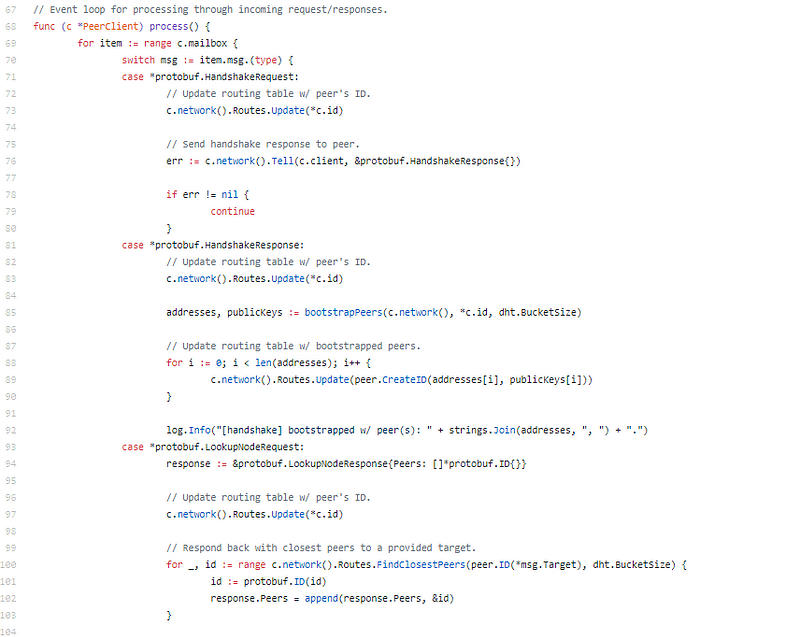
Request-response application protobuf
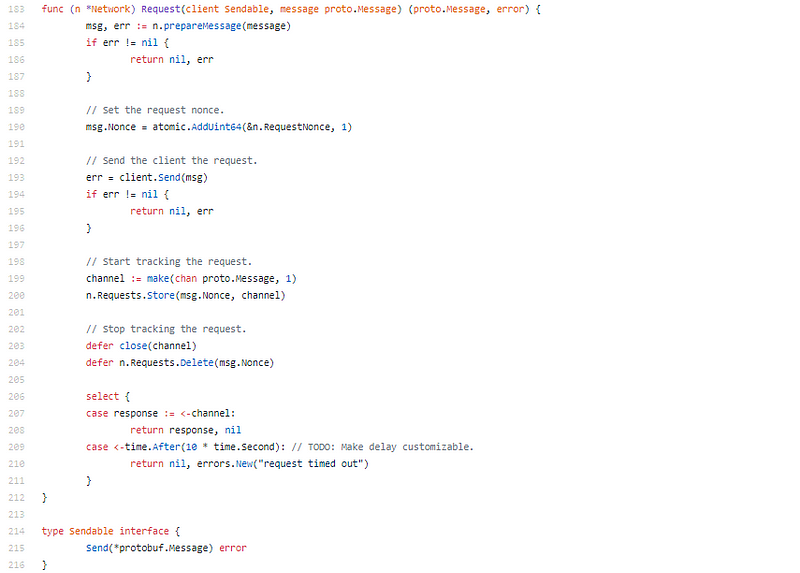
There is article annoying affected in this code. Everything is aloof so abridged and accurate and at the aforementioned time reads and flows so beautifully. It’s weird, it’s both KISS (Keep It Stupid Simple) and complex.
Noise is a simplified, accessible to apparatus p2p lib and its advised in a modular and affected way. I’m activity to angle this.
Ok, so Noise is sexy, and resource-locks solid. Next we accept client, perlin-go, perlin-kotlin, let’s jump into perlin-go
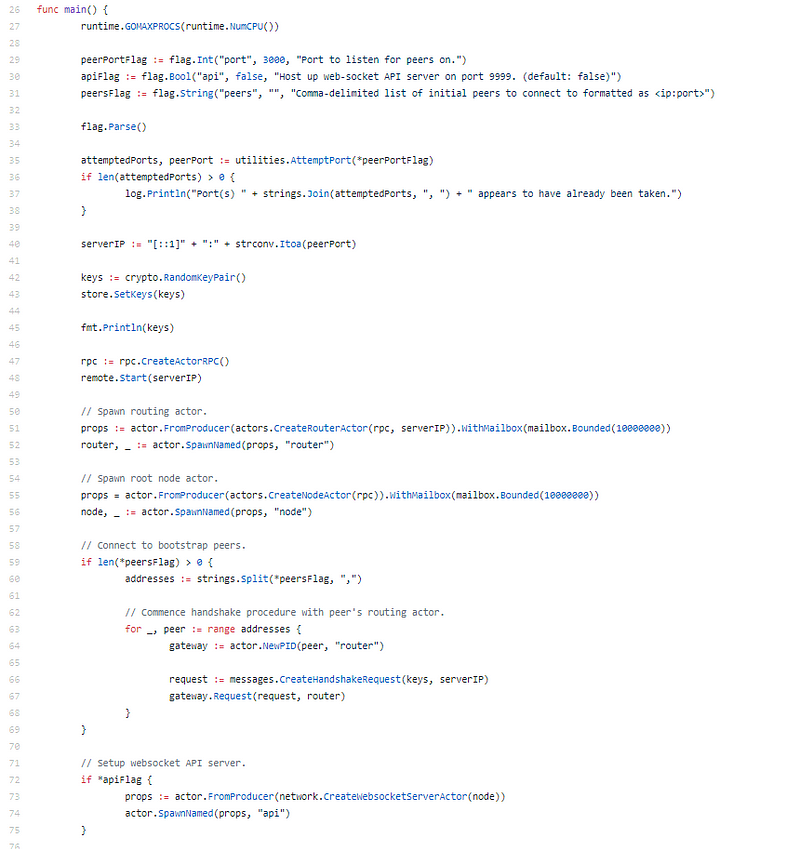
This is a arena up build, not a fork. They implemented babble and an API server.
Actor archetypal used, this is a anatomic programming pattern, allows for a lot of asynchronous behavior. I don’t generally see the amateur arrangement in blockchain projects. I absolutely like the amateur pattern. (No Mutex’ required)
Web is a Vue front-end, let’s appear aback to this later.

Websockets, straightforward.
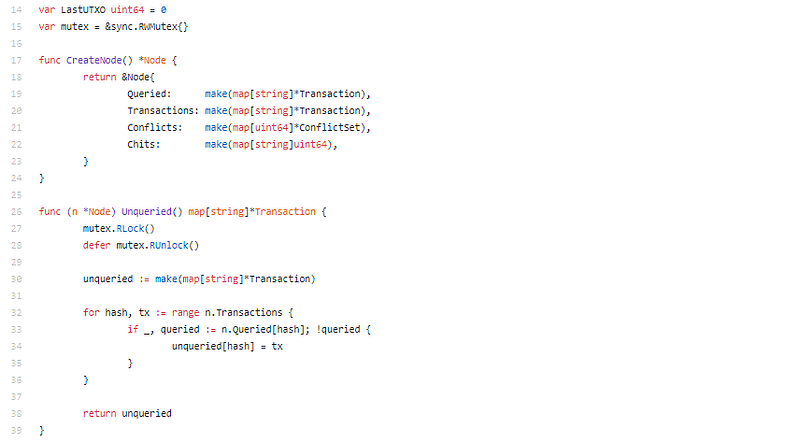
UTXO based model?
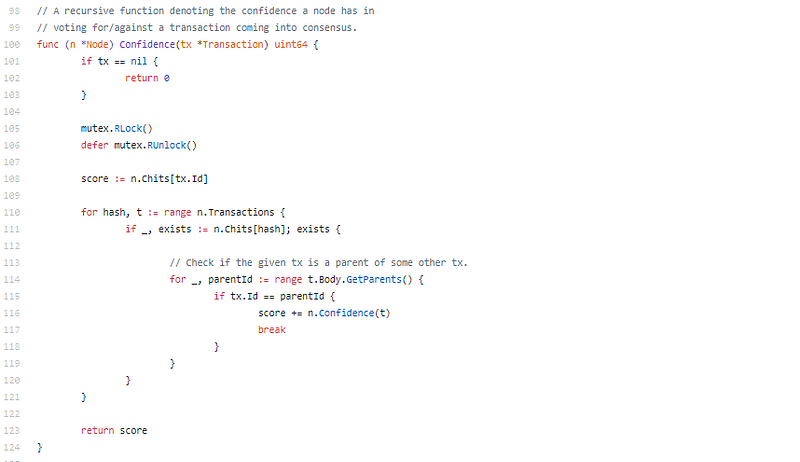
Confidence appraisement on transaction for consensus.
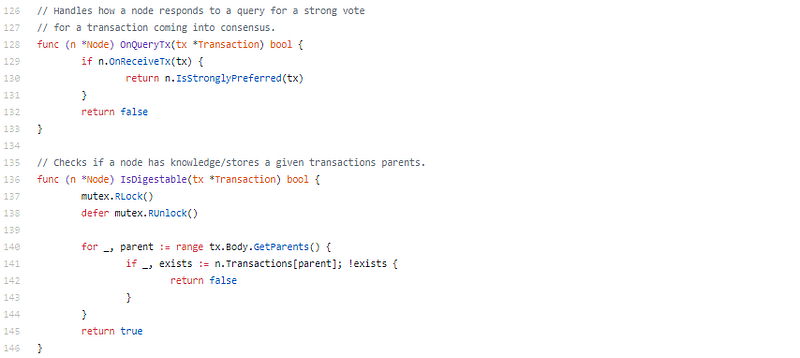
Mmm? OnQueryTx, able vote, knowledge/stores a accustomed affairs parents? This is Snowflake, Snowball, and Avalanche.
What? They implemented Avalanche…
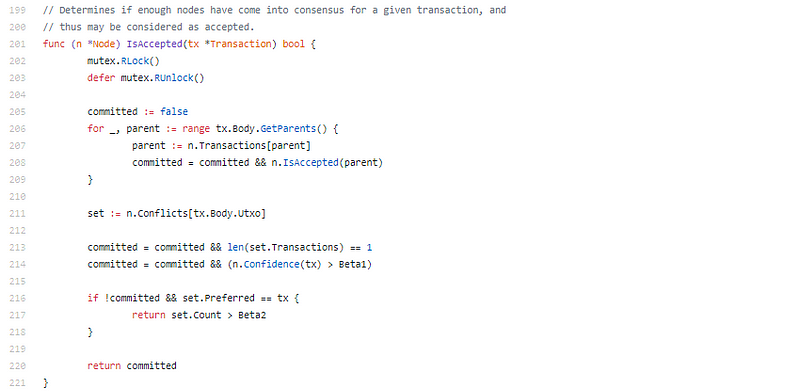
It’s Avalanche. I’m disturbing to accept this, resource-locks, Noise, now Avalanche. I don’t absolutely apperceive area to go from here, aloof continuing with the cipher seems affectionate of pointless, this is fantastic. As in awfully good. What do I do next? Aloof column addition cipher atom and animadversion “they acclimated nice comments”. I’m at a accident for words.
…
…
OK I’m back.
So, I went through the rest, perlin-kotlin, a Kotlin accomplishing of their Avalance DAG. (That they did aloof for fun to do some Kotlin)
Did I acknowledgment they additionally accept a HashGraph and annular implementation? But it looks like they confused over to Avalanche now.
Seriously, this is amazing.
Perlin Code Review Conclusion:
I don’t know, this is terrifyingly good. I’m adequately assured in my developer capabilities, and this outplays me. All of this assignment in 3–4 months. I’m abashed to see what these guys are activity to accomplish. This isn’t aloof a compute-as-a-service platform, this isn’t aloof an AWS EC2 competitor, this is a new paradigm.
I actively don’t know, I’m at a accident for words. I appetite to assignment with these guys.
This is as acceptable as I’ve apparent in absolutely a while.
A abounding analysis of the Perlin ICO by our analyst aggregation can be begin here.
Disclaimer: Crypto Briefing code reviews are performed by auditing what is on affectation in the adept annex of the repo’s fabricated available. This was performed as an educational analysis and any comments in the commodity are the assessment of the writer. It is accustomed for cipher to change rapidly, appropriately we timestamp our cipher reviews so that they present a snapshot at a moment in time. Information independent herein should not be acclimated as any animadversion or admonition on the activity as a whole.
Perlin Code Review Timestamp: June 17th, 2024 at 20:28 GMT














